Tuesday 16 July 2013
Posted by
Shubham
- 20:16
The IP Series!!--Video Tutorials.
The IP Series!!--Video Tutorials.
learn IPv6.
Facebook Page:-
Sunday 7 July 2013
Posted by
Shubham
- 22:32
Hacking and Pen-Testing With The Nokia 770/800/810/n8
Hacking and Pen-Testing With The Nokia 770/800/810/n8
Hacking and Pen-Testing With The Nokia 770/800/810 Notes:-
-------------------------------------------------------------------------------------
The n770 and n800 are Linux based
mobile devices from Nokia that are designed for portable web surfing, Internet
Tablets as Nokia calls them. The platform for these devices is know as Maemo and
since it's Linux based many hackers have extended its functionality greatly. Since both
models have built in WiFi and Bluetooth, and the older 770 model has come down
in price ($130 when I got mine), I've decided to use it as a mobile
pen-testing device. This page will be a collection of my notes on how to install
and run hacking/pen-testing software with the n800/n770/n810. This page is a very
rough draft for now, I plan to update it as I have more information to convey.
---------------------------------------------------------------------------------
The Operating System:
Obviously, the first thing you will need is the proper OS. For my notes, I'm using Internet Tablet OS 2007 Hacker Edition (abbreviate IT2007HE) on a Nokia 770. IT2007 is meant for the n800, but the Hacker Edition version will run on the n770. I'm hoping that by using this edition I'll be able to write notes that should work on both models. To install IT2007HE download it from:
Download:-
then use the installer from:Download:
When the installer asks what firmware to use, point it at the bin file you downloaded from Maemo.org. Everything else the installer should walk you through. For the record, I'm using SU-18_2007HACKER_4.2007.36-2_PR_F5_MR0_ARM.bin.
Adding Software
Maemo appears to be Debian based and uses the APT package management system. You can install software off the web by using repositories you download from, or by installing individual .debs from the RS-MMC card. You can set up repositories by hand if you wish, like in the following screen shots:
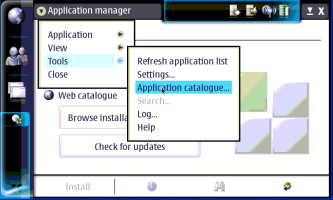
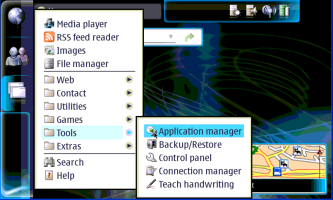
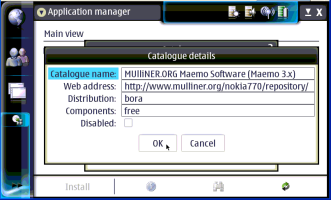
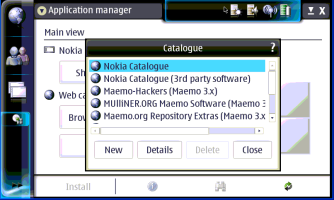
-----------------------------------------------
Once the repositories are set up you can install apps using the Application Manager and let it take care of the dependences for you. Just choose "Browse installable applications" and go through the alphabetical list, or use the binoculars icon to search for the package you want. It should be noted that to install some packages you will have to be in "Red Pill" mode. If you ever get an error that says you can't install something, put your tablet in "Red Pill" mode by going to add a new repository, typing just "matrix" in the web address line then hitting cancel and choosing Red as show in the screen shots below. If you want to find even more software for you 770/800 check out http://maemo.org/community/wiki/applicationrepositories/ .
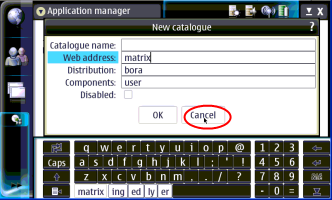
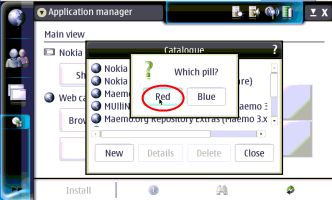
----------------------------------------------------------------------------------------------------------------------------------
Using the above repositories you should be able to add
pen-testing apps like Nmap, Kismet, Netcat and others.
Becoming Root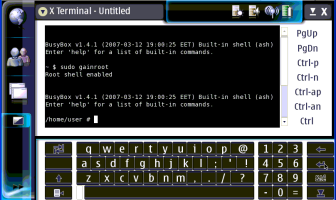

For some apps
like Kismet a Nmap, to get the full functionality you will have to become
root. The easiest way is to drop out to a command line using Xterm and type
"sudo gainroot" then use use whatever apps you like.
That's it for now, more to come later.
Do Comment
Posted by
Shubham
- 22:05
Damn Vulnerable Web App:-
Damn Vulnerable Web App:-
Damn Vulnerable Web App:-
------------------------------------------------
Upgrade Your Skills/;-
Download:-
Posted by
Shubham
- 22:00
Windows 8 Activator
Windows 8 Activator
----------------------------------------------------------------------------------------------------------------------------------------
No comments
You just download the rar file and open the file and run as administrator.
Posted by
Shubham
- 01:00
Adobe Photoshop 14.0 CC final 1.26 GB
Adobe Photoshop 14.0 CC final 1.26 GB
Adobe Photoshop 14.0 CC final 1.26 GB
----------------------------------------------
Adobe Photoshop CC final 14.0 1.26 GB Interface Language: English, Russian, French, Hungarian, Polish, Turkish, Czech, Ukrainian.
CC Adobe Photoshop - a program for processing raster images .. Supports numerous graphic formats. Adobe Photoshop allows you to create new images and edit them. Photoshop used to create photorealistic images to work with color scanned images, retouching, color correction, transformation of graphs, color separation, etc. Adobe Photoshop has all the methods of working with bitmaps, in this case, is to work with layers and uses contours. The program is the undisputed leader among the professional graphic editors due to its wide possibilities, high efficiency and speed. Adobe Photoshop provides all the necessary tools for correcting, editing, preparing images for printing and high quality output
. New features in Photoshop CC are listed below:
NEW Photoshop easy. Photoshop CC part of Creative Cloud ™ ®. Therefore, it is accessible to all users with the latest updates and access to new versions available from the date of issue. Publishing capabilities in the cloud allows you to organize your files on multiple computers. Through integration with the Behance ® can share their projects with other users directly from the CC program Photoshop and receive instant feedback on their work of designers from around the world. See more>
".. A variety of textures, sharp edges and clear details The new" Smart Sharpen "NEW The new" Smart Sharpen is the most modern technology to increase the sharpness of today. It analyzes the image, allowing you to maximize clarity, and significantly reduce noise and ghosting to create high-quality images that look natural
NEW increasing sampling smart .. Increase the low resolution image for use in print or image to the size of the average quality of the panel or a poster. A new feature allows you to keep the details up-sampling and sharpness quietly
. New advanced features. As a component of Creative Cloud, Photoshop app gives you the power of image editing and video editing, and also includes advanced tools for editing objects and analysis of three-dimensional images, previously only available Photoshop Extended
. NEW Camera Raw 8 and layer support. Apply Changes Camera Raw as a filter for layers and files in Photoshop, then upgrade layers and files that fit you well. In addition, with the new Adobe Camera Raw ® external module 8, you can correct more accurately the images, eliminate perspective distortion and create a thumbnail
. NEW variable rectangles with rounded corners. This is one of the most requested features. Now you can change the size of the numbers, as well as edit, both before and after its creation. You can even change the corner radius of rectangles. If the number is to be placed on a web page, you can export data from the CSS file to save time
. NEW Ability to simultaneously select multiple contours and shapes. Increase the efficiency of their business processes, quickly picking contours, shapes and vector masks in just a few clicks of the mouse. Even in a multi-document environment with lots of loops can easily find the right path (and film) directly onto the canvas, using the new filtering mode
. NEW camera image stabilization. Take photos even a mobile camera. If the image is blurred due to the slow shutter speed and a long focal length, the function "Image Stabilization camera," the trajectory analysis and restore the sharpness
. NEW Expanded support for smart objects. Apply effects, image blur and plastics with possible reversible patch with support for smart objects. Add blur, push, pull, wrinkles and swelling of the photos or videos, while retaining the ability to revert to the original file. Modify or remove the effects when you want, even after saving the file
. New improved design of three-dimensional objects. When you work with three-dimensional objects and textures to create interactive maps of the survey can now be up to 100 times faster. Thank you to the powerful mechanism for drawing in Photoshop, you can create stunning three-dimensional model
. New styles of improved policies. You spend hours on the overall design of the police. The use of font styles will keep the formatting as a template and then apply it with one click. You can even specify font styles for use in your documents
Photoshop . NEW copy CSS attributes. When creating a design code manually Web sites, you can always create elements such as rounded corners or color corresponding to the original. Photoshop can now create CSS for specific design elements. Simply copy and paste the code into your web editor to get the desired result
. New action under certain conditions. Automate routine operations using conventional machining operations. To automatically select different actions based on the rules you create in these commands are used if / then
. ". New and improved "3D scene with the ease of changing two dimensions to three dimensions through the edition" 3D scene display panel ", which contains a set of parameters familiar to you, with whom you have worked before in" layers "as" Duplicate "," Create an instance "," Groups "and" Delete "
. new features that help save time. Reduce time spent on routine tasks, thanks to the small, but offers very user-friendly, users are encouraged to realize. Quickly create contours with new keyboard shortcuts, mouse, move the edges of the space, including the ICC profiles in the PNG, and
. NEW 3D effects improved. Shadows and reflections can transform your 3D illustration of a masterpiece, and images interactively preview superior create memorable works even faster. In addition, you can now easily create light effects, stage lighting, emphasizing the contours and textures better
. New colors importing from files on the Web. Import color samples directly from HTML, CSS and SVG files. Change these samples as you wish or just use patterns ready colors are based on existing web content
. NEW font smoothing system. With the parameter that smooths the corresponding smoothing is implemented on the Mac or Windows ®, you can now create realistic insights that allow you to see how a font will look on your web pages
Year: .
2013 OS: Windows 7/8
Operating System: Microsoft Windows XP Service Pack 3, Windows Vista Home Premium, Business, Ultimate, Enterprise Service Pack 1 (Service Pack 2 recommended) Windows 7.
Download:-
Part 1
Part 2
Part 3
Part 4
Friday 5 July 2013
Posted by
Shubham
- 20:58
Work : Download AutoCad 2012
Work : Download AutoCad 2012
Work : Download AutoCad 201
-----------------------------------------------
Download below :
Download AutoCad
Posted by
Shubham
- 20:54
Win RAr 4.10 Beta 5 Portable(x64/x96)
Win RAr 4.10 Beta 5 Portable(x64/x96)
Win RAr 4.10 Beta 5 Portable(x64/x96).
----------------------------------------------
WinRAR 4.10 Beta 5 Portable (x86/x64) 2.2 MB.Features of WinRAR:
* Using WinRAR puts you ahead of the crowd when it comes to compression by consistently making smaller archives than the competition, saving disk space and transmission costs.
* WinRAR provides complete support for RAR and ZIP archives and is able to unpack CAB, ARJ, LZH, TAR, GZ, ACE, UUE, BZ2, JAR, ISO, 7Z, Z archives.
* WinRAR offers a graphic interactive interface utilizing mouse and menus as well as the command line interface.
* WinRAR supports NTFS file security and data streams.
* WinRAR is easier to use than many other archivers with the inclusion of a special "Wizard" mode which allows instant access to the basic archiving functions through a simple question and answer procedure. This avoids confusion in the early stages of use.
* WinRAR offers you the benefit of industry strength archive encryption using AES (Advanced Encryption Standard) with a key of 128 bits.
* WinRAR supports files and archives up to 8,589 billion gigabytes in size. The number of archived files is, for all practical purposes, unlimited.
* WinRAR offers the ability to create selfextracting and multivolume archives.
Recovery record and recovery volumes allow to reconstruct even physically damaged archives.
* WinRAR features are constantly being developed to keep WinRAR ahead of the pack.
Compatible with:All Windows (32/64-bit)
Download Here :
Posted by
Shubham
- 20:43
Adobe Dreamweaver CC 13.0 324.6 Mb Build 6390
Adobe Dreamweaver CC 13.0 324.6 Mb Build 6390
Adobe Dreamweaver CC 13.0 324.6 Mb Build 6390
-----------------------------------------------
CC Adobe Dreamweaver 13.0 Build 6390 324.6 Mb
Your favorite tools are about to get even better. Introducing
Creative Cloud ™ desktop applications, including Adobe ® Photoshop ®
and Illustrator ® DC DC. They are the next generation of tools
CS. Get hundreds of brand new features. New ways to keep your
creative universe in sync. And, as always, your applications
directly on your desktop, not in a browser and not in the
cloud . Mission control for creativity.
With Creative Cloud, all of your creative universe is
synchronized and organized for you across multiple devices.
Follow the comments posted on shared files, keep an eye
on your work and your followers on Behance ®, manage your
fonts, download the latest product updates, and more . Your one-stop publishing shop.
create and publish websites, mobile sites, iPad and
other content of any medium or device applications.
You can even create a customized portfolio with
ProSite, included free with your paid subscription.
With Creative Cloud, you have all the tools and
services you need to share what you create with an
audience of hundreds, thousands, even millions . Master a new medium.
Creative Cloud includes everything you need to
experience like never before. Guests have access
to all Adobe creative tools and service with a
library of more and more video tutorials to help
you discover new tools and rapid ramp. If you've
always wanted to diversify and create websites,
applications, videos, and more, now you can . Built to scale.
Collaborate. Grow. Change. It's easy with
Creative Cloud for teams. Add or reassign
seats in minutes. Give everyone the latest
versions of the same tools. Never worry about
compatibility. And transparently share files
from any device with 100GB of cloud storage.
Posted by
Shubham
- 20:36
TuneUp.Utilities.2012.v12.0.2120.7 Full Version
TuneUp.Utilities.2012.v12.0.2120.7 Full Version
The new Start page
TuneUp Utilities 2011 welcomes you with a completely redesigned Start page, which tells you about the status of your computer. If problems or nonoptimal settings are found, you are only a mouse-click away from resolving them. The Start page also tells you when new tips for increasing computer performance are available and warns you if maintenance tasks are not being taken care of automatically. The Start page also shows you whether new automatic startup programs have been added to Windows since the last time you ran TuneUp Utilities. You can decide whether these programs that start up automatically are really necessary.
TuneUp Speed Optimizer
Which settings slow your computer down? Which unnecessary services or programs are running in the background? Is your Internet connection optimally configured? TuneUp Speed Optimizer knows the answers to all these questions. It examines your entire system for bottlenecks, superfluous background programs, and incorrect settings. Great: with just one click you can carry out most optimizations very quickly. In addition, TuneUp Speed Optimizer provides suggestions for speeding up your system.
TuneUp Shortcut Cleaner
Cleaning up your working environment is tedious: removing invalid shortcuts from the Start menu, the Desktop, and the Quick Launch bar is very time-consuming. TuneUp ShortCut Cleaner now does the work for you. It checks whether all shortcuts are valid and removes the orphaned ones with just a click of a button. At the same time, empty folders are removed from the Start menu. TuneUp ShortCut Cleaner also checks frequently used programs and cleans up the list of recently opened files.
Support for the Opera browser
After hard disk defragmentation, which we introduced in TuneUp Utilities 2009, the feature most requested by customers was support for the Opera browser. TuneUp Utilities 2010 now also includes full support for Opera. Via several special Opera settings, TuneUp System Control now allows you to change the number of Speed Dial entries, conveniently choose your default search engine, and reenable fast backward and forward navigation. Internet optimization lets you optimize Opera's performance for your Internet connection. Free up disk space lets you delete the Opera cache.
And Many More
Download Here :
Posted by
Shubham
- 20:32
DriverPack Solution 13 Full Version [ for all windows ]
DriverPack Solution 13 Full Version [ for all windows ]
DriverPack Solution 13 Full Version [ for all windows ]
-----------------------------------------------
DriverPack Solution 13 - is the latest version of the most popular program to automatically install the drivers. This version contains a number of new features and optimized for all platforms (x86-x64), and significantly simplifies the process of reinstalling Windows on virtually any computer. You will now be spared the trouble of finding and installing drivers, reducing them to a few clicks!
Automatic installation of drivers:
Install the DriverPack Solution on almost any computer for only about 5 minutes.
Saving of time
After downloading the Driver Pack Solution once no longer need to spend time searching for drivers.
Windows XP / Vista / 7 (x86-x64)
Supports all modern operating systems!
As a 32-and 64-bit version
Ease of use
Simple and intuitive interface.
Any driver for any computer
All the drivers on a single DVD-ROM
Simplify downloading new drivers from the Internet.
Ability to update drivers
Update the existing driver to more recent versions.
The program is suitable for all models of computers.
That includes free drivers for laptops: Asus, Acer, Sony, Samsung, HP, Lenovo, Toshiba, Fujitsu-Siemens, DELL, eMachines, MSI .
Download
Download:
Passwd:www.tknowmore.blogspot.com
Posted by
Shubham
- 20:02
Free Download : CEH [ Certified Ethical Hacker Ebooks ] -
Free Download : CEH [ Certified Ethical Hacker Ebooks ] -
Free Download : CEH [ Certified Ethical Hacker Ebooks ] -
-----------------------------------------------
1: Student Introduction
2: Introduction to Ethical Hacking
3: Hacking Laws
4: Footprinting
5: Google Hacking
6: Scanning
7: Enumeration
8: System Hacking
9: Trojans and Backdoors
10: Viruses and Worms
11: Sniffers
12: Social Engineering
13: Phishing
14: Hacking Email Accounts
15: Denial of Service
16: Session Hijacking
17: Hacking Webservers
18: Web Application Vulnerabilities
19: Web based Password Cracking Techniques
20: SQL Injection
21: Hacking Wireless Networks
22: Physical Security
23: Linux Hacking
24: Evading IDS Firewall and Honeypot
25: Buffer Overflows
26: Cryptography
27: Penetration Testing
28: Writing Virus Codes
29: Assembly Language Tutorial
30: Exploit Writing 1
31: Exploit Writing 2
32: Exploit Writing 3
33: Reverse Engineering Techniques
34: MAC OS X Hacking
35: Hacking Routers, Cable Modems and Firewalls
36: Hacking Mobile Phones, PDA and Handheld Devices
37: Bluetooth Hacking
38: VoIP Hacking
39: RFID Hacking
40: Spamming
41: Hacking USB Devices
42: Hacking Database Servers
43: Cyber Warfare- Hacking Al-Qaida and Terrorism
44: Internet Content Filtering Techniques
45: Privacy on the Internet
46: Securing Laptop Computers
47: Spying Technologies
48: Corporate Espionage by Insiders
49: Creating Security Policies
50: Software Piracy and W
51: Hacking and Cheating Online Games
52: Hacking RSS and Atom.
53: Hacking Web Browsers
54: Proxy Server Technologies
55: Preventing Data Loss
56: Hacking Global Positioning System
57: Computer Forensics and Incident Handling
58: Credit Card Frauds
59: How to Steal Passwords
60: Firewall Technologies
61: Threats and Countermeasures
62: Case Studies
63: Botnets
64: Economic Espionage
65: Patch Management
67: Security Convergence
68: Identifying the Terrorists
69: prova 312-50
70: CEH - Classroom Lab Setup v6 -
& Many More:--
Download:
1st Part
2nd Part
3rd Part
4th Part
5th Part
6th Part
Password:- Maya Badmash
Password:- Maya Badmash
Posted by
Shubham
- 19:52
Chrome Crypter v5.3 Free Download [ 100% FUD ] UPDATED -
Chrome Crypter v5.3 Free Download [ 100% FUD ] UPDATED -
Chrome Crypter v5.3 Free Download [ 100% FUD ] UPDATED -
--------------------------------------------------------------------------------------------------------------------------------
Chrome
Crypter v5.3 Free Download [ 100% FUD ] UPDATED - See more at:
http://blackhatcrackers.blogspot.in/2013/03/chrome-crypter-v53-free-download-100.html#sthash.TZl9Mu1P.dpuf
Posted by
Shubham
- 19:43
Encrypting Your Hard disk!!
Encrypting Your Hard disk!!
Encrypting Your Hard disk!!
Using True Crypt:-
Get it From Here:-
----------------------------------------------
Creating A Volume
Step 1: Download TC and open it.
Step 2: Click any "letter" and press create volume. - See more at: http://blackhatcrackers.blogspot.in/2013/06/how-to-encrypt-your-hard-drive.html#sthash.vuf0RVk6.dpuf
Step 1: Download TC and open it.
Step 2: Click any "letter" and press create volume. - See more at: http://blackhatcrackers.blogspot.in/2013/06/how-to-encrypt-your-hard-drive.html#sthash.vuf0RVk6.dpuf
Creating A Volume
Step 1: Download TC and open it.
Step 2: Click any "letter" and press create volume. -
As Shown In Above Image!!
Step 3: Now click next 3 times.
Step 3: Now click next 3 times.
Step 4: Now press select file and save it somewhere hidden, for this tutorial I saved it to my desktop. -
Step 5: Now click next with the settings I have on this picture Step 8: Now once you are at this part, move your mouse in the box of True Crypt, this is a must -
Step 9: Now you will have a file like this, be sure to keep this file in a hidden place. Do Not Lose It.
-----------------------------------------------------------------------------------------------------------------------------
Opening The Volume:-
Step 1: Press select file and find your file, then click on mount.
Step 2: Now Put Your Password ..
Step 3:Now U Shud See like Above image!!Now Go to Your Computer you Should See a Hidden Drive ,You Can Store Anything What You Want!!
----------------------------------------------------------------------
Posted by
Shubham
- 19:24
Websploit Toolkit!!--
Websploit Toolkit!!--
WebSploit Is An Open Source Project For Scan And Analysis Remote System From Vulnerability
[+]Autopwn - Used From Metasploit For Scan and Exploit Target Service
[+]wmap - Scan,Crawler Target Used From Metasploit wmap plugin
[+]format infector - inject reverse & bind payload into file format
[+]phpmyadmin - Search Target phpmyadmin login page
[+]lfi - Scan,Bypass local file inclusion Vulnerability & can be bypass some WAF
[+]apache users - search server username directory (if use from apache webserver)
[+]Dir Bruter - brute target directory with wordlist
[+]admin finder - search admin & login page of target
[+]MLITM Attack - Man Left In The Middle, XSS Phishing Attacks
[+]MITM - Man In The Middle Attack
[+]Java Applet Attack - Java Signed Applet Attack
[+]MFOD Attack Vector - Middle Finger Of Doom Attack Vector
[+]USB Infection Attack - Create Executable Backdoor For Infect USB For Windows
Posted by
Shubham
- 19:22
Netool.sh V2.4 Released:-
Netool.sh V2.4 Released:-
Netool.sh V2.4 Released:-

New modules:
1)webcrawler.py
2)Agressive Directory Scanner
3)Fast Directory Scanner
4)Admin Page Finder
5)WebShell.php Scanner
6)File Upload Scanner
[nmap]
7)Scan List.txt of targets
Description of the script:-
netool.sh is a script in bash to automate frameworks like Nmap,Driftnet,SSLstrip, and ettercap MITM attacks, Retrieves metadata, geo-location of target, changes hostname, change IP and Mac-Address to decoy scans, search for admin login page on taget website, search for directorys inside target website, search for webshells.php planted on website and scan Common URL File Upload vulns, also capture pictures of web-browser surfing of the target machine, perform TCP/UDP packets manipulation using etter.filters, DoS attacks local/external network,also uses metasploit [msfpayload+msfencode+msfcli] to gain control of target machine ...
Home project
See WIKI :
DOWNLOAD LINK:
Enjoy, and save hacking .
Posted by
Shubham
- 19:20
Ebook
The best guide to the Metasploit Framework.
The best guide to the Metasploit Framework.
"The best guide to the Metasploit
Framework."
—HD Moore, Founder of the Metasploit
Project
The Metasploit Framework makes discovering, exploiting, and sharing vulnerabilities quick and relatively painless. But while Metasploit is used by security professionals everywhere, the tool can be hard to grasp for first-time users. Metasploit: The Penetration Tester's Guide fills this gap by teaching youhow to harness the Framework and interact with the vibrant community of Metasploit contributors.
Once you've built your foundation for penetration testing, you'll learn the Framework's conventions, interfaces, and module system as you launch simulated attacks. You'll move on to advanced penetration testing techniques, including network reconnaissance and enumeration, client-side attacks, wireless attacks, and targeted social-engineering attacks.
Learn how to:
Find and exploit unmaintained, misconfigured, and unpatched systems
Perform reconnaissance and find valuable information about your target
Bypass anti-virus technologies and circumvent security controls
Integrate Nmap, NeXpose, and Nessus with Metasploit to automate discovery
Use the Meterpreter shell to launch further attacks from inside the network
Harness standalone Metasploit utilities, third-party tools, and plug-ins
Learn how to write your own Meterpreter post exploitation modules and scripts
You'll even touch on exploit discovery for zero-day research, write a fuzzer, port existing exploits into the Framework, and learn how to cover your tracks. Whether your goal is to secure your own networks or to put someone else's to the test, Metasploit: The Penetration Tester's Guide will take you there and beyond.
Download Link:
Posted by
Shubham
- 19:19
python
Violent Python:-
Violent Python:-
Violent Python:-
Violent Python shows
you how to move from a theoretical understanding of offensive computing
concepts to a practical implementation. Instead of relying on another
attacker's tools, this book will teach you to forge your own weapons
using the Python programming language. This book demonstrates how to
write Python scripts to automate large-scale network attacks, extract
metadata, and investigate forensic artifacts. It also shows how to write
code to intercept and analyze network traffic using Python, craft and
spoof wireless frames to attack wireless and Bluetooth devices, and how
to data-mine popular social media websites and evade modern anti-virus.
-
Demonstrates how to write Python scripts to automate large-scale
network attacks, extract metadata, and investigate forensic artifacts.
-
Write code to intercept and analyze network traffic using Python. Craft
and spoof wireless frames to attack wireless and Bluetooth devices.
- Data-mine popular social media websites and evade modern anti-virus.
Download Link:
Posted by
Shubham
- 19:18
<<Back|Track 5 Cook Book->>
Back|Track 5 Cook Book-
<<Back|Track 5 Cook Book->>
Over 80 recipes to execute many of the best known and little known penetration testing aspects of BackTrack 5
Learn to perform penetration tests with BackTrack 5
Nearly 100 recipes designed to teach penetration testing principles and build knowledge of BackTrack 5 Tools
Provides detailed step-by-step instructions on the usage of many of BackTrack's popular and not-so- popular tools
In Detail
BackTrack
is a Linux-based penetration testing arsenal that aids security
professionals in the ability to perform assessments in a purely native
environment dedicated to hacking. BackTrack is a distribution based on
the Debian GNU/Linux distribution aimed at digital forensics and
penetration testing use. It is named after backtracking, a search
algorithm.
"BackTrack 5 Cookbook" provides you with practical recipes
featuring many popular tools that cover the basics of a penetration
test: information gathering, vulnerability identification, exploitation,
priviledge escalation, and covering your tracks.
The book begins by covering the installation of BackTrack 5 and setting up a virtual environment to perform your tests.
We
then dip into recipes involving the basic principles of a penetration
test such as information gathering, vulnerability identification, and
exploitation. You will further learn about privilege escalation, radio
network analysis, Voice over IP, Password cracking, and BackTrack
forensics.
"BackTrack 5 Cookbook" will serve as an excellent source of information for the security professional and novice alike.
What will you learn from this book
Install and set up BackTrack 5 on multiple platforms
Customize BackTrack to fit your individual needs
Exploit vulnerabilities found with Metasploit
Locate vulnerabilities Nessus and OpenVAS
Provide several solutions to escalate privileges on a compromised machine
Learn how to use BackTrack in all phases of a penetration test
Crack WEP/WPA/WPA2 Encryption
Learn how to monitor and eavesdrop on VOIP networks
Approach
This
is a cookbook with the necessary explained commands and code to learn
BackTrack thoroughly. It smoothes your learning curve through organized
recipes.
Who this book is written for
This book is for anyone who
desires to come up to speed in using BackTrack 5 or for use as a
reference for seasoned penetration testers.
Posted by
Shubham
- 19:14
c
C++ by Dissection
Download 50+ Hacking Ebooks Collection.
C++ by Dissection
C++ by Dissection presents a thorough introduction to the programming process by carefully developing working programs to illuminate key features of the C++ programming language. This book presents the concepts of the programming process using the "dissection" method, the hallmark feature that has made Ira Pohl's C and Java books of the "By Dissection" series so popular. Dissection is a unique pedagogical tool first developed by the author to point out key features of program code. It is similar to a structured walk-through of the code, with the intention of explaining newly encountered programming elements and idioms as found in working code. The book includes a CD-ROM containing a compiler and an electronic version of the book that allows readers to search, take notes, and highlight right on their computer. Each chapter presents a number of carefully explained programs, which lead the reader in a holistic manner to ever-improving programming skills. Right from the start, the reader is introduced to complete programs, and at an early point in the book, the reader is introduced to writing functions as a major feature of structured programming. It contains four to seven small code dissections per chapter, and then each chapter culminates with a larger, extended code dissection. "Software Engineering" sections in each chapter reinforce sound software engineering skills. The book assumes no programming background and can be used by first-time computer users or by experienced programmers who are transitioning to C++.
Download Link:
Posted by
Shubham
- 19:14
O'Reilly HTTP Definitive Guide
O'Reilly HTTP Definitive Guide
-O'Reilly HTTP Definitive Guide-
Behind every web transaction lies the Hypertext
Transfer Protocol (HTTP) --- the language of web browsers and servers,
of portals and search engines, of e-commerce and web services.
Understanding HTTP is essential for practically all web-based
programming, design, analysis, and administration.
While the basics
of HTTP are elegantly simple, the protocol's advanced features are
notoriously confusing, because they knit together complex technologies
and terminology from many disciplines. This book clearly explains HTTP
and these interrelated core technologies, in twenty-one logically
organized chapters, backed up by hundreds of detailed illustrations and
examples, and convenient reference appendices. HTTP: The Definitive
Guide explains everything people need to use HTTP efficiently --
including the "black arts" and "tricks of the trade" -- in a concise and
readable manner.
In addition to explaining the basic HTTP features,
syntax and guidelines, this book clarifies related, but often
misunderstood topics, such as: TCP connection management, web proxy and
cache architectures, web robots and robots.txt files, Basic and Digest
authentication, secure HTTP transactions, entity body processing,
internationalized content, and traffic redirection.
Many technical
professionals will benefit from this book. Internet architects and
developers who need to design and develop software, IT professionals who
need to understand Internet architectural components and interactions,
multimedia designers who need to publish and host multimedia,
performance engineers who need to optimize web performance, technical
marketing professionals who need a clear picture of core web
architectures and protocols, as well as untold numbers of students and
hobbyists will all benefit from the knowledge packed in this volume.
There
are many books that explain how to use the Web, but this is the one
that explains how the Web works. Written by experts with years of design
and implementation experience, this book is the definitive technical
bible that describes the "why" and the "how" of HTTP and web core
technologies. HTTP: The Definitive Guide is an essential reference that
no technically-inclined member of the Internet community should be
without.
Sunday 30 June 2013
Posted by
Shubham
- 15:52
List of website for researching!
List of website for researching!
List of website for researching!
All links of website below, everybody can use it for search document or e-books and video learning for supporting your studying too. ^^
----------------------------------------------
http://www.ebookshare.net/
http://booktraining.im/
http://www.topdg.com/
http://www.downarchive.com/
http://devxstudios2.org/
http://www.the-dll.com/
http://
http://www.ddl-turkey.net/
http://www.bookspark.net/
http://dnhome.us/
http://sunbox-it.com/
http://
http://knowfree.net/
http://latestsharing.com/
http://ebook68.com/
http://
http://
http://www.euro-share.com/
http://sharingcentre.net/
http://www.downturk.info/
http://www.ebook-section.com/
http://www.technoezine.com/
http://ebooksplanet.net/
http://
http://www.euro-share.com/
http://www.freebookspot.es/
http://sevno.org/
http://allathere.com/
http://rapid4all.org/
http://
http://worldsdown.net/
http://www.kickassgfx.net/
http://ainkklgrhm.typepad.com/
http://downeu.net/
http://www.gfxtra.com/
http://www.graphixshare.com/
http://devxstudios2.org/
http://
http://worldsdown.net/
http://ebooksplanet.net/
http://www.dl4all.com/
http://ebookee.org/
http://ebook3000.org/
http://
http://www.ebook4download.com/
http://mashable.com/
http://www.heroturko.com/
http://hotmegaupload.com/
http://www.downextra.com/
http://booktraining.im/
http://feeds.feedburner.com/
http://
http://
http://www.wowebook.co/
http://iwannafile.com/
http://tags.softarchive.net/
http://www.byhero.com/
http://
http://
http://www.iwannafile.com/
http://
http://www.filesfeed.com/
http://keyshara.ru/
http://filecrop.com/
http://torrentz.eu/
http://devxstudios2.org/
http://www.the-dll.com/
http://
http://www.ddl-turkey.net/
http://www.bookspark.net/
http://dnhome.us/
http://sunbox-it.com/
http://
http://knowfree.net/
http://latestsharing.com/
http://ebook68.com/
http://
http://
http://www.euro-share.com/
http://sharingcentre.net/
http://www.downturk.info/
http://www.ebook-section.com/
http://www.technoezine.com/
http://ebooksplanet.net/
http://
http://www.euro-share.com/
http://www.freebookspot.es/
http://sevno.org/
http://allathere.com/
http://rapid4all.org/
http://
http://worldsdown.net/
http://www.kickassgfx.net/
http://ainkklgrhm.typepad.com/
http://downeu.net/
http://www.gfxtra.com/
http://www.graphixshare.com/
http://devxstudios2.org/
http://
http://worldsdown.net/
http://ebooksplanet.net/
http://www.dl4all.com/
http://ebookee.org/
http://ebook3000.org/
http://
http://www.ebook4download.com/
http://mashable.com/
http://www.heroturko.com/
http://hotmegaupload.com/
http://www.downextra.com/
http://booktraining.im/
http://feeds.feedburner.com/
http://
http://
http://www.wowebook.co/
http://iwannafile.com/
http://tags.softarchive.net/
http://www.byhero.com/
http://
http://
http://www.iwannafile.com/
http://
http://www.filesfeed.com/
http://keyshara.ru/
http://filecrop.com/
http://torrentz.eu/
Saturday 29 June 2013
Posted by
Shubham
- 17:09
Shells --- Hack The Server..
Shells --- Hack The Server..
Shells --- Hack The Server..
-------------------------------------------------------------------------------------
We all know When we hack any website we need shell's to get the root of the domain/Sever where we Can Symlink/Deface/Download Or do anything What u want . .
Get it Right Now ..
Password Is Jaihind
Download & Enjoy Hacking
Posted by
Shubham
- 17:01
NetStumbler
NetStumbler
~NetStumbler~
-----------------------------------
Find all available wireless networks.
___________________________________
Subscribe to:
Posts (Atom)
Labels
- <<Back|Track 5 Cook Book->> (1)
- Admin Control Panel Finder v 1 & --Admin CPanel Finder--:- (1)
- Adobe Dreamweaver CC 13.0 324.6 Mb Build 6390 (1)
- Adobe Photoshop 14.0 CC final 1.26 GB (1)
- Adobe Photoshop CS2 (1)
- Alcohol 52% (1)
- Alleycode HTML Editor 2.21 (1)
- AntiVirus (5)
- ASCII Animator 1.9 (1)
- Auto-Cad For Dummies.. (1)
- avast! Free Antivirus 8.0.1489 (1)
- Avira AntiVir Personal - Free Antivirus 13.0.0.3185 (1)
- Bluestack (1)
- Browsers (1)
- c (1)
- C++ by Dissection (1)
- Chrome Crypter v5.3 Free Download [ 100% FUD ] UPDATED - (1)
- Comodo Dragon 28.0.4.0 (1)
- Connectify (Windows 7) (1)
- DAEMON Tools Lite 4.47.1 (1)
- Damn Vulnerable Web App:- (1)
- Download 50+ Hacking Ebooks Collection. (2)
- DriverPack Solution 13 Full Version [ for all windows ] (1)
- Ebook (1)
- Encrypting Your Hard disk!! (1)
- Fedora Linux 19 (32-Bit) (1)
- Free Download : CEH [ Certified Ethical Hacker Ebooks ] - (1)
- Free Ringtone Maker Portable 2.4.0.1324 (1)
- GatherProxy 5.9 (1)
- Hacking and Pen-Testing With The Nokia 770/800/810/n8 (1)
- InSIDDer~~ Discover the Wi-Fi networks around you (1)
- Instagiffer 1.32 (1)
- Internet Security (3)
- Introduction (1)
- IPInfoOffline 1.32 (1)
- Linux-Ubuuntu (1)
- List of website for researching! (1)
- Macromedia Flash 8 (1)
- McAfee AVERT Stinger 11.0.0.425 (1)
- MCShield 2.7.4 (1)
- Microsoft Office Accounting Express 2009 (2)
- Microsoft Security Essentials (32-Bit) 4.2.223.0 (1)
- Microsoft Security Essentials (64-Bit) 4.2.223.0 (1)
- Microsoft Visual Web Developer 2008 Express (1)
- MySQL for Windows 5.6.12 (1)
- Netool.sh V2.4 Released:- (1)
- NetStumbler (1)
- NOD 32 Keys .. (1)
- O'Reilly HTTP Definitive Guide (1)
- Office (1)
- PhoneClean 2.2.2 (1)
- PortScan 1.42 (1)
- Proxy Finder Premium Daily Update 2013 v1.0 Final 5.86 Mb (1)
- PuTTy:- A Free SSH & Telnet Client:- (1)
- python (1)
- Realtek High Definition Audio Codec Driver for 2000/XP/2003 v2.71 (1)
- RealWorld Cursor Editor 2013.1 (1)
- Shells --- Hack The Server.. (1)
- Sysinternals Autoruns 11.62 (1)
- TCP Optimizer (1)
- TCPView (1)
- TeamViewer (1)
- The best guide to the Metasploit Framework. (1)
- The IP Series!!--Video Tutorials. (1)
- TinyWall 2.1.3 (1)
- TuneUp.Utilities 2013 (1)
- TuneUp.Utilities.2012.v12.0.2120.7 Full Version (1)
- TV 4.0 (1)
- Violent Python:- (1)
- Websploit Toolkit!!-- (1)
- Win RAr 4.10 Beta 5 Portable(x64/x96) (1)
- Windows 8 Activator (1)
- Windows 8 Transformation Pack 7.0 (1)
- WordPress 3.6 Beta 3 / 3.5.1 (1)
- Work : Download AutoCad 2012 (1)
Amazon
Pages
Blog Archive
Games
Google Search
Login/Register
Creative Common License

Hacks by Shubham Shah is licensed under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License.
Based on a work at http://downloadshacks001.blogspot.com.
Permissions beyond the scope of this license may be available at https://adf.ly/PhduS
Follow us on FaceBook
Popular Posts
-
Chrome Crypter v5.3 Free Download [ 100% FUD ] UPDATED - -------------------------------------------------------------------------...
-
P roxy Finder Premium Daily Update 2013 v1.0 Final 5.86 Mb Proxy Finder Premium Update Daily 2013 v1.0 Final 5.86 Mb . Proxy Finder Pr...
-
Admin Control Panel Finder v 1 & --Admin CPanel Finder-- : - ---------------------------------- Admin Panel Finder By Sh...
-
Free Download : CEH [ Certified Ethical Hacker Ebooks ] - ----------------------------------------------- 1: Student Introduction ...
-
LibreOffice 4.1.1:- ----------------------------------------------------------- LibreOffice is the free power-packed Open S...
-
Fedora Linux 19 (32-Bit) :- ----------------------------------------------------------------------------------------------------------...
-
PhoneClean 2.2.2 :- ------------------------------------------------------------------------------------- Publisher's Descrip...
-
"The best guide to the Metasploit Framework." —HD Moore, Founder of the Metasploit Project The Metasploit Frame...
-
Ubuntu Latest Free Download :- -------------------------------------------------------------------------------- Get The latest ...
-
DriverPack Solution 13 Full Version [ for all windows ] ----------------------------------------------- DriverPack Solution 13 - is t...
Total Pageviews
Labels
- <<Back|Track 5 Cook Book->> (1)
- Admin Control Panel Finder v 1 & --Admin CPanel Finder--:- (1)
- Adobe Dreamweaver CC 13.0 324.6 Mb Build 6390 (1)
- Adobe Photoshop 14.0 CC final 1.26 GB (1)
- Adobe Photoshop CS2 (1)
- Alcohol 52% (1)
- Alleycode HTML Editor 2.21 (1)
- AntiVirus (5)
- ASCII Animator 1.9 (1)
- Auto-Cad For Dummies.. (1)
- avast! Free Antivirus 8.0.1489 (1)
- Avira AntiVir Personal - Free Antivirus 13.0.0.3185 (1)
- Bluestack (1)
- Browsers (1)
- c (1)
- C++ by Dissection (1)
- Chrome Crypter v5.3 Free Download [ 100% FUD ] UPDATED - (1)
- Comodo Dragon 28.0.4.0 (1)
- Connectify (Windows 7) (1)
- DAEMON Tools Lite 4.47.1 (1)
- Damn Vulnerable Web App:- (1)
- Download 50+ Hacking Ebooks Collection. (2)
- DriverPack Solution 13 Full Version [ for all windows ] (1)
- Ebook (1)
- Encrypting Your Hard disk!! (1)
- Fedora Linux 19 (32-Bit) (1)
- Free Download : CEH [ Certified Ethical Hacker Ebooks ] - (1)
- Free Ringtone Maker Portable 2.4.0.1324 (1)
- GatherProxy 5.9 (1)
- Hacking and Pen-Testing With The Nokia 770/800/810/n8 (1)
- InSIDDer~~ Discover the Wi-Fi networks around you (1)
- Instagiffer 1.32 (1)
- Internet Security (3)
- Introduction (1)
- IPInfoOffline 1.32 (1)
- Linux-Ubuuntu (1)
- List of website for researching! (1)
- Macromedia Flash 8 (1)
- McAfee AVERT Stinger 11.0.0.425 (1)
- MCShield 2.7.4 (1)
- Microsoft Office Accounting Express 2009 (2)
- Microsoft Security Essentials (32-Bit) 4.2.223.0 (1)
- Microsoft Security Essentials (64-Bit) 4.2.223.0 (1)
- Microsoft Visual Web Developer 2008 Express (1)
- MySQL for Windows 5.6.12 (1)
- Netool.sh V2.4 Released:- (1)
- NetStumbler (1)
- NOD 32 Keys .. (1)
- O'Reilly HTTP Definitive Guide (1)
- Office (1)
- PhoneClean 2.2.2 (1)
- PortScan 1.42 (1)
- Proxy Finder Premium Daily Update 2013 v1.0 Final 5.86 Mb (1)
- PuTTy:- A Free SSH & Telnet Client:- (1)
- python (1)
- Realtek High Definition Audio Codec Driver for 2000/XP/2003 v2.71 (1)
- RealWorld Cursor Editor 2013.1 (1)
- Shells --- Hack The Server.. (1)
- Sysinternals Autoruns 11.62 (1)
- TCP Optimizer (1)
- TCPView (1)
- TeamViewer (1)
- The best guide to the Metasploit Framework. (1)
- The IP Series!!--Video Tutorials. (1)
- TinyWall 2.1.3 (1)
- TuneUp.Utilities 2013 (1)
- TuneUp.Utilities.2012.v12.0.2120.7 Full Version (1)
- TV 4.0 (1)
- Violent Python:- (1)
- Websploit Toolkit!!-- (1)
- Win RAr 4.10 Beta 5 Portable(x64/x96) (1)
- Windows 8 Activator (1)
- Windows 8 Transformation Pack 7.0 (1)
- WordPress 3.6 Beta 3 / 3.5.1 (1)
- Work : Download AutoCad 2012 (1)
Webutation-badge
Amazon
Powered by Blogger.
About The Author
- Shubham































